sid history
Hello All,
Hope this post finds you in good health and spirit.
SID History
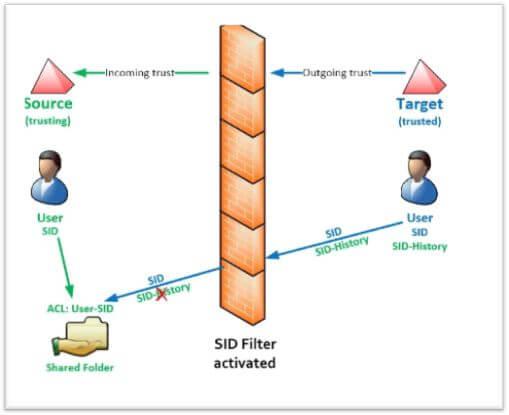
SID History is an attribute in Active Directory (AD) that provides backward compatibility when a resource in the previous domain hasn’t had its permissions changed. Several checklist for Active Directory migration tools state that when objects are migrated from other domains, SID History is written. It makes it possible for old Access Control List (ACL) items to continue after migration.
To assist businesses in upgrading from Windows NT 4.0 to Active Directory, SID History was first included in Windows Server 2000. And it certainly sped it up and simplified migrations.
SIDs ensure that each security principal is unique inside an Active Directory domain. Reusing them exposes systems that rely on SID-based ACLs at risk of having illegal access.
Many businesses decide they wish to maintain the extra set of keys.
They declare that migration is over. Just preserve the SID History, I say. We won’t be changing the keys on our source AD. With the old key, we now have two keys that match.
The issue is that, like in the case mentioned above, the prior owner may return and break into the new home using the spare key. Alternately, a SID History injection might be carried out using mimikatz or a similar tool to allow impersonation of any users or groups, including Enterprise Admins. This type of manipulation may provide people better access to neighborhood resources.
Microsoft Active Directory Migration Tool (ADMT—currently version 2.0) uses the ClonePrincipal API to add the old SID to the SID History attribute of the new SID. You can download ADMT for free from the Microsoft Web site.
So, that’s all in this blog. I will meet you soon with next stuff. Have a nice day!!!
Recommended content
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Disabling and enabling replication on schema master domain controller
How to enable strict replication consistency
How to prevent lingering objects replication in active directory
AD replication process overview
How to force active directory replication
Change notification in replication process
How to check replication partner for a specific domain controller
dcdiag test replications
Guys please don’t forget to like and share the post.Also join our WindowsTechno Community and where you can post your queries/doubts and our experts will address them .
You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.