An account with the same name exists in Active Directory
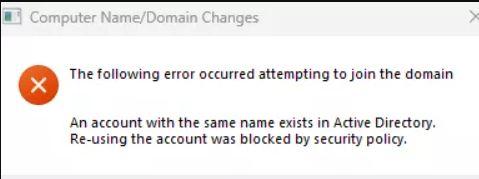
An account with the same name exists in Active Directory. Re-using the account was blocked by security policy
This post is regarding “An account with the same name exists in Active Directory. Re-using the account was blocked by security policy”
After installing the windows cumulative updates on October 11, 2022, it started to seem that domain join with computer account reuse can intentionally fail with the following error;-
Error 0xaac (2732): NERR_AccountReuseBlockedByPolicy: “An account with the same name exists in Active Directory. Re-using the account was blocked by security policy.”
An account with the same name exists in Active Directory.
Legacy behavior
Before you install the October 11, 2022, or later cumulative updates, the client computer queries Active Directory for an existing account with the same name. This query occurs during domain join and computer account provisioning. If such an account exists, the client will automatically attempt to reuse it.
Note The reuse attempt will fail if the user who try to attempt the domain join operation does not have the sufficient write permissions. However, if the user has enough permissions the domain join will complete.
New behavior
Once install the October 11, 2022, or after that Windows cumulative updates on a client computer, during domain join, the client will perform additional security checks before attempting to re-use the existing computer account in active directory.
Algorithm:
- Account re-use attempt will be permitted if the user attempting the operation is the creator of the existing account.
- Account re-use attempt will be permitted if the account was created by a member of domain administrators.
These additional security checks required before attempting to join the computer. If the checks are successful, the rest of the join operation is subject to Active Directory permissions as before. This change does not affect new accounts.
Note After installing the October 11, 2022, or later Windows cumulative updates, domain join with computer account reuse might intentionally fail with the following error:
Error 0xaac (2732): NERR_AccountReuseBlockedByPolicy: “An account with the same name exists in Active Directory. Re-using the account was blocked by security policy.”
If so, the account is intentionally being protected by the new behavior. Event ID 4101 will be triggered once the error above occurs and the issue will be logged in c:\windows\debug\netsetup.log. Please follow the steps below in Take Action to understand the failure and resolve the issue.
Resolution
There are four ways to fix this problems.
- Rename the computer and join using a different account that doesn’t already exist.
- Perform the join operation using the same account that created the computer account in the target domain.
- Uninstall the problematic KB5020276 Windows Update from domain controllers to fix the problem.
- If you don’t want to make any changes to domain controllers so, create the NetJoinLegacyAccountReuse registry to re-use the existing computer account.
1. Review computer account provisioning workflows and understand if changes are required.
- If the existing account is stale (unused), delete it before attempting to join the domain again. As we know this only effect the old accounts, not new account if we recreate the account in active directory then try to join the computer with domain, it works.
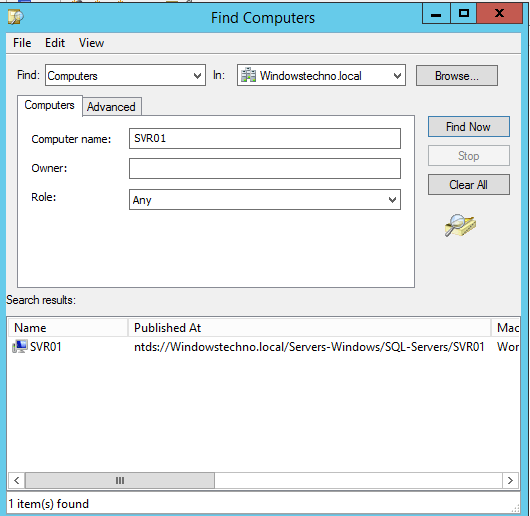
Open the Active directory user and computer console and Search for the object for which you are receiving the error message during domain joining.
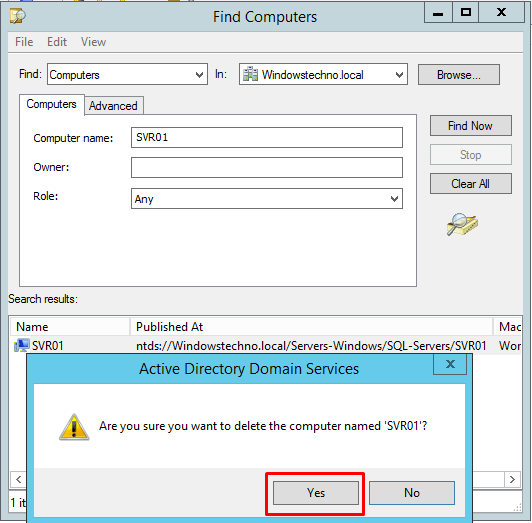
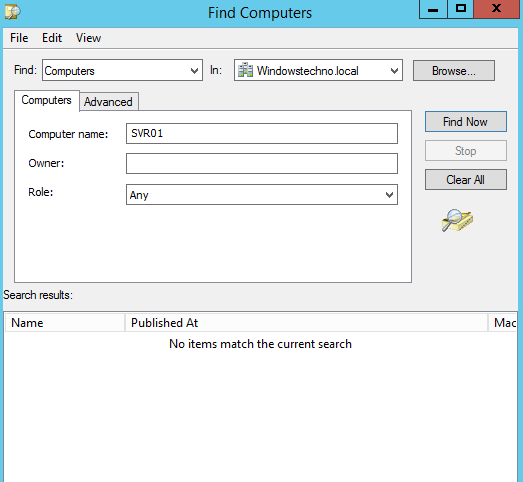
Delete the object from Active Directory.
Click on Yes.
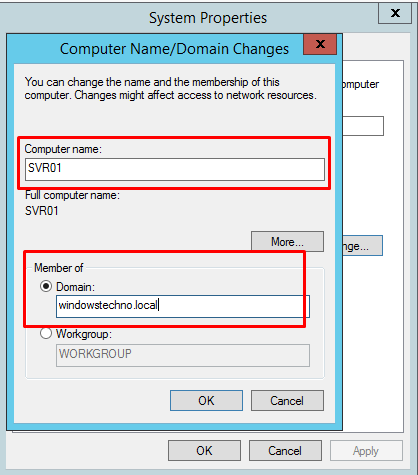
Now go to server and try to join with domain. Type the domain name and click on OK.
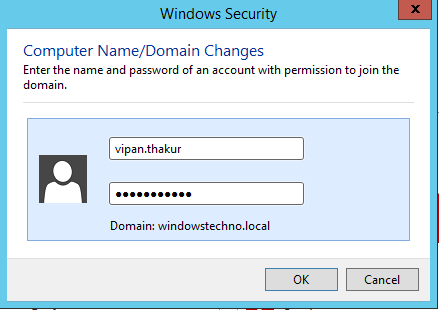
Please type the username and password that has access to join the computer with domain.
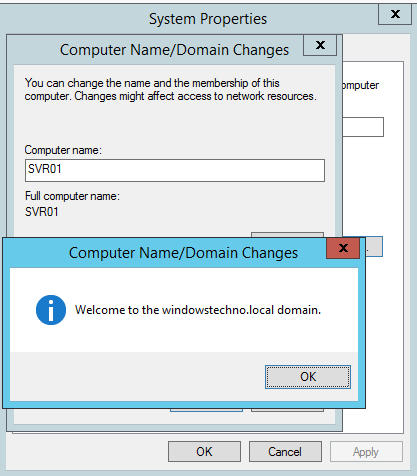
Once you click on OK , it will be joined with domain .
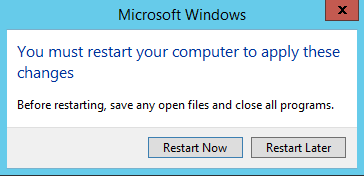
Restart the server and enjoy.
This is recommended approach, and it should be followed by tech engineers. By using the workaround suggested in this article, you may also resolve it.
2. Uninstall the KB5020276 Windows Update
- Press Windows + I key to open the Settings app.
- Navigate to the Windows Update tab and click on Update history.
- Click the Uninstall updates button and select the KB5020276 update.
- Click on Uninstall and wait while the process completes.
- Restart your PC and try reusing the account to see if it creates another user in the Domain.
- Uninstalling the KB5020276 Microsoft update will remove the additional security checks on the domain join process. It permits reuse attempts without bothering about meeting the criteria.
3. Rename the computer and join using a different account that doesn’t already exist.
The issue is only coming on existing accounts, not for new accounts, if you don’t want to make any changes to domain controllers as well on machine where you are getting the error message, just rename machine name to different one and try to join the machine with domain, it works.
Perform the join operation using the same account that created the computer account in the target domain.
4. Create the NetJoinLegacyAccountReuse registry to re-use the existing computer account
If the existing account is owned by a trusted security principal and an administrator wants to reuse the account, they might do so by temporarily setting the following registry key at the individual client computer level. Then immediately remove the registry setting after the join operation is complete. No restart is necessary for changes to the registry key to take effect.
The following registry entry can be temporary set at the level of each client machine if the current account is controlled by a trusted security principal and the administrator wants to reuse the account.
Once the join process is finished, delete the registry setting right away. The registry key may be changed without attempting to restart the computer.
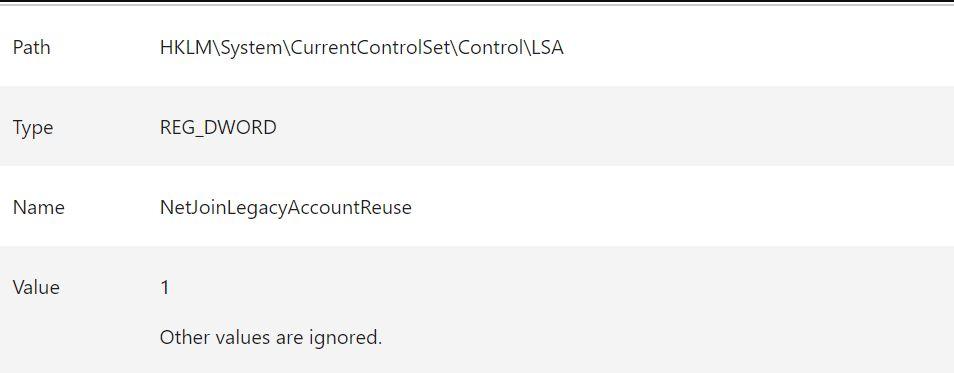
| Path | HKLM\System\CurrentControlSet\Control\LSA |
| Type | REG_DWORD |
| Name | NetJoinLegacyAccountReuse |
| Value | 1 Other values are ignored. |
Launch the Registry Editor of the appropriate device, create the key, then change the value above to set the key. If the key does not already exist, you might need to generate it. Please access the Registry Path shown below.
HKLM\System\CurrentControlSet\Control\LSA
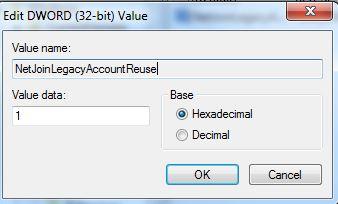
As you can see, “NetJoinLegacyAccountReuse” is a DWORD Value that does not yet exist. It will have to be made by myself.
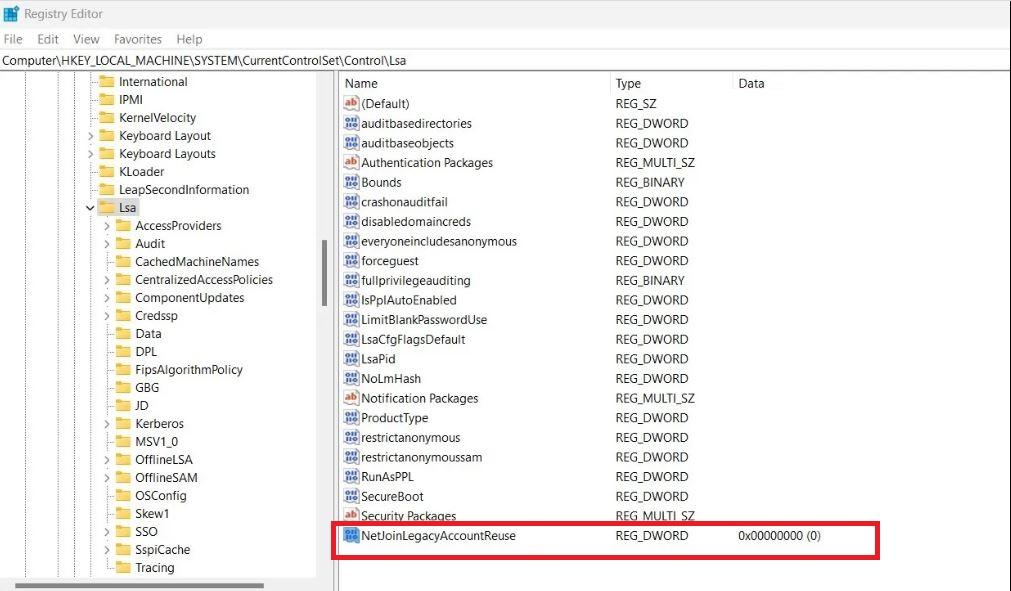
Change the DWORD you just generated and add the value 1 there.
You don’t need to restart the server; simply attempt to join it to a domain. This solution will resolve your domain joining problem.
Known issues
| Issue 1 | After installing the September 12, 2023 or after updates, domain join may fail in your environments where the following policy is set: Network access – Restrict clients allowed to make remote calls to SAM – Windows Security This is because now client machines make authenticated SAMRPC calls to the domain controller to perform security verification checks related to re-using computer accounts. Example from a netsetup.log where this issue occurred: 09/18/2023 13:37:15:379 NetpDsValidateComputerAccountReuseAttempt: returning NtStatus: c0000022, NetStatus: 5 09/18/2023 13:37:15:379 NetpDsValidateComputerAccountReuseAttempt: returning Result: FALSE 09/18/2023 13:37:15:379 NetpCheckIfAccountShouldBeReused: Active Directory Policy check with SAM_DOMAIN_JOIN_POLICY_LEVEL_V2 returned NetStatus:0x5. 09/18/2023 13:37:15:379 NetpCheckIfAccountShouldBeReused:fReuseAllowed: FALSE, NetStatus:0x0 09/18/2023 13:37:15:379 NetpModifyComputerObjectInDs: Account exists and re-use is blocked by policy. Error: 0xaac 09/18/2023 13:37:15:379 NetpProvisionComputerAccount: LDAP creation failed: 0xaac |
| Issue 2 | If the computer owner account has been deleted, and an attempt to reuse the computer account occurs, Event 16997 will be logged in the System event log. If this occurs, it is okay to re-assign ownership to another account or group. |
| Issue 3 | If only the client has the March 14, 2023 or later update, the Active Directory policy check will return 0x32 STATUS_NOT_SUPPORTED. Previous checks that were implemented in the November hotfixes will apply as shown below: NetpGetADObjectOwnerAttributes: Looking up attributes for machine account: CN=LT-NIClientBA,CN=Computers,DC=contoso,DC=com NetpGetADObjectOwnerAttributes: Ms-Ds-CreatorSid is empty. NetpGetNCData: Reading NC data NetpReadAccountReuseModeFromAD: Searching '<WKGUID=AB1D30F3768811D1ADED00C04FD8D5CD,DC=LT2k16dom,DC=com>' for '(&(ObjectClass=ServiceConnectionPoint)(KeyWords=NetJoin*))'. NetpReadAccountReuseModeFromAD: Got 0 Entries. Returning NetStatus: 0, ADReuseMode: 0 IsLegacyAccountReuseSetInRegistry: RegQueryValueEx for 'NetJoinLegacyAccountReuse' returned Status: 0x2. IsLegacyAccountReuseSetInRegistry returning: 'FALSE''. NetpDsValidateComputerAccountReuseAttempt: returning NtStatus: c00000bb, NetStatus: 32 NetpDsValidateComputerAccountReuseAttempt: returning Result: FALSE NetpCheckIfAccountShouldBeReused: Active Directory Policy check returned NetStatus:0x32. NetpCheckIfAccountShouldBeReused:fReuseAllowed: FALSE, NetStatus:0x0 NetpModifyComputerObjectInDs: Account exists and re-use is blocked by policy. Error: 0xaac NetpProvisionComputerAccount: LDAP creation failed: 0xaac |
FAQs
How to reset the computer account that already exists in Active Directory?
In the Active Directory Users and Computers MMC (DSA), you can right-click the computer object in the computers or appropriate container and then click Reset Account. This resets the machine account.
What does an account name with the same name exists in Active Directory?
The client computer queries Active Directory for an existing account with the same name. This query occurs during domain join and computer account provisioning. If such an account exists, the client will automatically attempt to reuse.
What happens when you reset an account in Active Directory?
This resets the machine account. Resetting the password for domain controllers using this method is not allowed. Resetting a computer account breaks that computer’s connection to the domain and requires it to rejoin the domain.
What happens if you duplicate a computer name in Active Directory?
In active directory, you can’t have two computer objects with same name. When you disjoint a computer from domain or reset its computer object, the computer object will not be deleted and can be reused to rejoin the same or another computer with same name.
Can we Rename an Active Directory account?
Open the Active Directory Users and Computers snap-in. In the left pane, right-click on the domain and select Find. Type the name of the user and click Find Now. In the Search Results, right-click on the user and select Rename.
Can two users have the same name in Active Directory?
You can’t create two computer accounts with the same name in Active Directory. A better way to avoid this problem is to have unique algorithms for computer account names.
So, that’s all in this blog. I will meet you soon with next stuff. Have a nice day!!!
Guys please don’t forget to like and share the post. Also join our WindowsTechno Community and where you can post your queries/doubts and our experts will address them.
You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.