RDP Port
RDP Port
Microsoft developed the proprietary Remote Desktop Protocol to offer customers a graphical interface for connecting to other computers through a network connection. For this, the user uses RDP client software, while the other machine has to be running RDP server software.
RDP port number is 3389 which provides network access for a remote user over an encrypted channel.
Before opening the RDP port, bear in mind the following.
- Strong Password Policies: Enforce strong password requirements for user accounts and discourage the use of default or easily guessable passwords.
- Two-Factor Authentication (2FA): Implement two-factor authentication, which adds an extra layer of security by requiring an additional verification step, such as a code sent to a mobile device, along with the password.
- Network Level Authentication (NLA): Enable NLA, a security feature that requires users to authenticate before establishing a remote desktop connection. It helps prevent unauthorized access attempts.
- Use SSL/TLS Encryption: Configure RDP to use SSL/TLS encryption for secure communication between the client and server. This helps protect data confidentiality during transit.
- Firewall Protection: Configure firewalls to allow RDP traffic only from trusted IP addresses or networks. Restricting access to RDP ports (default: TCP port 3389) helps minimize the risk of unauthorized access.
- Regular Updates and Patches: Keep the RDP client and server systems up to date with the latest security patches and updates. This helps address any known vulnerabilities.
- Account Lockout Policies: Implement account lockout policies to automatically lock out user accounts after a certain number of failed login attempts. This helps prevent brute-force attacks.
- Limit User Access: Grant RDP access only to authorized users who need it for their specific roles. Regularly review and revoke access for users who no longer require remote access.
- Session Timeouts: Configure session timeouts to automatically disconnect idle RDP sessions after a specific period of inactivity. This reduces the risk of unauthorized access if a session is left unattended.
- Monitor and Audit: Implement logging and monitoring mechanisms to track RDP connection attempts and activities. Regularly review logs for any suspicious or unauthorized access attempts.
Configure SSL/TLS encryption for RDP
Configuring SSL/TLS encryption for Remote Desktop Protocol (RDP) involves obtaining and installing an SSL certificate on the RDP server. Here’s a general overview of the steps involved:
- Obtain an SSL Certificate: Acquire an SSL certificate from a trusted certificate authority (CA). You can choose between a self-signed certificate or a certificate issued by a recognized CA. It is generally recommended to use a certificate from a trusted CA to ensure widespread client compatibility.
- Install the SSL Certificate: Install the SSL certificate on the RDP server. The exact steps may vary depending on the operating system and RDP server software being used. Typically, it involves importing the certificate into the server’s certificate store.
- Configure RDP to Use SSL/TLS: Enable SSL/TLS encryption in the RDP server settings. The process may differ depending on the specific RDP server software being used. Typically, you need to specify the SSL certificate to be used for encryption.
- Configure Firewall and Port Forwarding: Ensure that your firewall allows incoming connections on the SSL/TLS port (default: TCP port 3389) and forwards them to the RDP server.
- Test the SSL/TLS Connection: Verify the SSL/TLS configuration by connecting to the RDP server using an RDP client that supports SSL/TLS encryption. Ensure that the connection is established successfully.
It’s important to note that the specific steps for configuring SSL/TLS encryption for RDP may vary depending on the operating system and RDP server software being used. It is recommended to refer to the documentation or support resources provided by the specific RDP server software or consult with your system administrator for detailed instructions tailored to your environment.
Additionally, be sure to keep the SSL certificate up to date, renewing it as necessary, and regularly update the RDP server software to address any security vulnerabilities and take advantage of the latest security features.
You can check the current port by running the following PowerShell command:
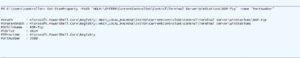
Get-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "PortNumber"
For example:
PS C:\Users\controller> Get-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "PortNumber"
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations
PSChildName : RDP-Tcp
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
PortNumber : 3389
What port need to open to allow remote desktop?
TCP port 3389 has to be open in order to use Remote Desktop. Moreover, with RDP 8.0, acceleration is enabled by opening UDP port 3389.
The port that the terminal server (or PC being connected) uses can be changed. It is not possible to modify the UDP port individually since it utilises the same port number as the TCP option.
Since RDP 8.0 (included with Windows 8 and Windows Server 2012, and accessible through an update for Windows 7 and Windows Server 2008 R2), UDP acceleration has been made available.
We can set custom RDP port numbers using following path.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
How to Change the Remote Desktop Port on Windows?
- Open the Registry Editor (
regedit.exe) and go to the registry key HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp; - Find the DWORD parameter with the name PortNumber. This parameter shows the port, on which the Remote Desktop service is listening. The default is 3389 (decimal);
- Change the value of this parameter. I have changed the RDP port to 3390.
- If your machine has a Windows Firewall, you will need to create a new rule that enables inbound connections to your new RDP port.
- In the Windows Defender Firewall panel, you may manually create an allowed incoming rule for your new TCP/UDP RDP port.
- Reboot your computer.
- You must provide the new RDP connection port in your mstsc.exe client to connect to this Windows host using Remote Desktop.
You may also change the RDP port by running the PowerShell command below. The new RDP port will be 3390 in this command.
$portvalue = 3390
Set-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "PortNumber" -Value $portvalue
New-NetFirewallRule -DisplayName 'RDPPORTLatest-TCP-In' -Profile 'Public' -Direction Inbound -Action Allow -Protocol TCP -LocalPort $portvalue
New-NetFirewallRule -DisplayName 'RDPPORTLatest-UDP-In' -Profile 'Public' -Direction Inbound -Action Allow -Protocol UDP -LocalPort $portvalue
So, that’s all in this blog. I will meet you soon with next stuff .Have a nice day !!!
Recommended contents
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Disabling and enabling replication on schema master domain controller
How to enable strict replication consistency
How to prevent lingering objects replication in active directory
AD replication process overview
How to force active directory replication
Change notification in replication process
How to check replication partner for a specific domain controller
dcdiag test replications
Guys please don’t forget to like and share the post.Also join our WindowsTechno Community and where you can post your queries/doubts and our experts will address them .
You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.